Cyber Security Alerts
- Home
- Cyber Warfare Defense Toolkit
- Cyber Security Alerts
The Latest Cyber Security News and Information
Stay up-to-date with the latest news, scam reports and tips to help mitigate your risk of a cyber attack.
October – Cybersecurity Infrastructure Security Agency (CISA) announces Secure Our World.
Every day, we are more and more connected—whether messaging family and friends, shopping online, or ordering supplies for our small businesses. It’s important to take steps to stay safe when using our phones, laptops, and smart devices. We Can Secure Our World by taking simple actions each day when connected.
This year CISA offers four easy steps to stay safe online:
Recognize & Report Phishing
Phishing often tries to get us to open a harmful attachment or share personal information. Learn what to look for to avoid the "phish hook."
Use Strong Passwords
Using strong passwords and a password manager are some easy ways to protect ourselves from someone logging into an account and stealing data or money.
Turn on MFA
Multifactor authentication means using more than a password to access an app or account. With MFA, we might be asked to enter a text code or use a fingerprint. It makes us much safer from someone accessing our accounts.
Update Software
Don't delay software updates. Flaws in software can give criminals access to files or accounts. Programmers fix these flaws as soon as they can, but we must install updates for the latest protection!
CISA.gov - https://www.cisa.gov/secure-our-world
October – Cybersecurity Infrastructure Security Agency (CISA) announces #StopRansomware Guide
Ransomware is a form of malware designed to encrypt files on a device, rendering them and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption. Over time, malicious actors have adjusted their ransomware tactics to be more destructive and impactful and have also exfiltrated victim data and pressured victims to pay by threatening to release the stolen data. The application of both tactics is known as “double extortion.” In some cases, malicious actors may exfiltrate data and threaten to release it as their sole form of extortion without employing ransomware.
This guide is an update to the Joint Cybersecurity and Infrastructure Security Agency (CISA) and Multi-State Information Sharing & Analysis Center (MS-ISAC) Ransomware Guide released in September 2020 (see What’s New) and was developed through the JRTF. This guide includes two primary resources:
Part 1: Ransomware and Data Extortion Prevention Best Practices
Part 2: Ransomware and Data Extortion Response Checklist
CISA.ov - https://www.cisa.gov/sites/default/files/2023-10/StopRansomware-Guide-508C-v3_1.pdf
August - QR Code-based Phishing Attains 587% Hike
The FBI is issuing a warning and making everyone aware of malicious QR codes spreading around that could steal personal information.
QR codes are common convenience businesses, airlines, ticket vendors, and others use. A smartphone’s camera can scan this square barcode to provide quick access to a website where you can learn about a product, share information, make a payment, prompt an application download, or get rewards and discounts.
The FBI said criminals are hijacking QR codes by placing stickers with codes they created over the top of the real QR code. The malicious code would direct victims to phishing websites where personal or financial information can be stolen.
The FBI offers several ways QR code users can protect themselves:
- Do not scan a code if it is on a sticker, looks like it has been replaced, or is covered up.
- After scanning the code, see if the URL you are taken to is a secure one that begins with “https.”
- Download a QR Code Scanner app that can help you recognize a suspicious code.
- Rather than scanning a code that will take you to a specific website, if possible, just type in the URL for that website.
To report QR code fraud, contact your local FBI field office and to the FBI Internet Crime Complaint Center. More information about QR code fraud can be found on the Attorney General’s website.
August - FBI issues credential stuffing attack warning
The FBI is warning U.S. organizations about credential-stuffing attacks that are being automated and concealed with the use of configurations and proxies.
"In particular, media companies and restaurant groups are considered lucrative targets for credential stuffing attacks due to the number of customer accounts, the general demand for their services, and the relative lack of importance users place on these types of accounts," the FBI said.
Username and password "combo lists" and configurations could be bought by threat actors from forums. Meanwhile, proxies could be leveraged for IP address obfuscation, noted the FBI.
"In some instances, actors conduct credential stuffing attacks without the use of proxies, requiring less time and financial resources to execute. Some cracking tools, including one of the most popular automated attack tools, allow actors to run the software without proxies," said the bureau, which also recommended the implementation of multi-factor authentication and good password hygiene to circumvent such attacks.
What is Credential Stuffing?
Credential stuffing is the automated injection of stolen username and password pairs (“credentials”) into website login forms to fraudulently gain access to user accounts. Since many users will re-use the same password and username/email, when those credentials are exposed (by a database breach or phishing attack, for example), submitting those sets of stolen credentials to dozens or hundreds of other sites can allow an attacker to compromise those accounts too.
Credential Stuffing is a subset of the brute force attack category. Brute forcing will attempt to try multiple passwords against one or multiple accounts, guessing a password, in other words. Credential Stuffing typically refers to specifically using known (breached) username / password pairs against other websites.
What is the Likelihood of this activity?
• Credential stuffing is one of the most common techniques used to take-over user accounts. It is dangerous to consumers and enterprises because of the ripple effects of these breaches.
How to Prevent Credential Stuffing
• Multi-factor authentication (MFA) is by far the best defense against the majority of password-related attacks, including credential stuffing and password spraying, with analysis by Microsoft suggesting that it would have stopped 99.9% of account compromises.
• Identifying Leaked Passwords. When creating a new password on an application, checking it against a list of known weak passwords, it can also be checked against passwords that have previously been breached. The most well-known public service for this is Pwned Passwords.
• Notifications of unusual security events. When suspicious or unusual activity is detected, if available, set up an alert to notify or warn you of the activity.
- owasp.org
- fbi.gov
Increase in Spear Phishing Attacks
March, 2022
Spear phishing is an increasingly common form of phishing that makes use of information about a target to make attacks more specific and “personal”. These attacks may, for instance, refer to their targets by their specific name or job position, instead of using generic titles like in broader phishing campaigns. According to a Trend Micro report 94% of targeted emails use malicious file attachments as the payload or infection source. The remaining 6% use alternative methods such as installing malware through malicious links.
The most commonly used file types for spear phishing attacks accounted for 70% of them. The main file types were .RTF (38%), .XLS (15%) and .ZIP (13%). Executable (.EXE) files were not as popular among cybercriminals because emails with .EXE file attachments are usually detected and blocked by security systems, said Trend. They also said that 75% of email addresses for spear phishing targets are easily found through web searches or using common email address formats.” – knowbe4.com
Important:
- Exercise caution if it is necessary to open emails with generic subject lines.
- Always be suspicious of unexpected emails, especially regarding financial or delivery correspondence, documents, or links.
- Verify important or potentially legitimate attachments with the sender via alternative means (e.g by phone or in-person) before opening them.
- Never configure Microsoft Office to enable macros by default & do not enable macros in Microsoft Office attachments.
Russian Invasion of Ukraine Leads to Increased Cybersecurity Threats
February, 2022
The Russian invasion of Ukraine, including alleged cyberattacks impacting the Ukrainian financial sector, have resulted in multiple government cybersecurity agencies releasing notices to the U.S. and global financial sector to strengthen cyber defenses in anticipation of broader cyberattacks.
Below are some of the recommendations for all US companies:
- Patch all vulnerabilities highlighted by U.S. CISA. https://www.cisa.gov/uscert/ncas/alerts/aa21-209a
- Raise awareness of basic cyber hygiene across organizations https://www.cisa.gov/cisa-cybersecurity-awareness-program
- Ensure that cybersecurity/IT personnel are focused on identifying and quickly assessing any unexpected or unusual network behavior. https://www.cisa.gov/shields-up
- Implement Cybersecurity Measures to protect your company - https://www.cisa.gov/sites/default/files/publications/CISA_Insights-Implement_Cybersecurity_Measures_Now_to_Protect_Against_Critical_Threats_508C.pdf
Apple patches several zero-day vulnerabilities
September, 2021
Apple recently released patches for three zero-day security vulnerabilities. These vulnerabilities impacting a range of iPhone and iPad models, including iPhone 5s, iPhone 6, iPhone 6 Plus, iPad Air, iPad mini 2, iPad mini 3, and sixth-generation iPod touch's.
“A malicious application may be able to execute arbitrary code with kernel privileges,” the company said. “Apple is aware of reports that an exploit for this issue exists in the wild.”
Keeping your software up to date is one of the most important things you can do to maintain your Apple product's security. Owners of Apple devices must update their mobile devices as soon as possible.
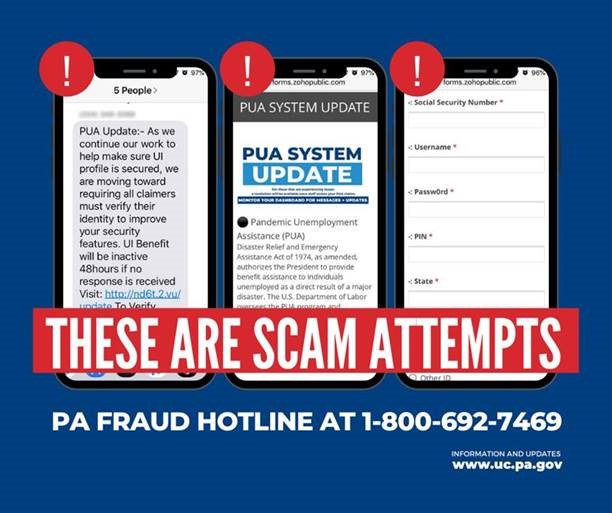
Pandemic Unemployment Assistance - Fraud Alert
April 13, 2021
The Pennsylvania Department of Labor & Industry’s security vendor has identified additional phishing attempts and fraud scams leveraging social media, text messaging, and email to lure unsuspecting individuals into providing personal information so that the scammers can claim their identity for Pandemic Unemployment Assistance (PUA).
The most recent scams include but are not limited to telling individuals they’ve won contests, won a cash prize, being eligible for a monetary award for applying for benefits, or offering an alternative or “faster” application or mobile app to apply for regular unemployment or PUA benefits.
- ATTN: Scammers are asking PUA claimants to verify their identity via text messages/web forms -- THIS IS A SCAM! (see below for example)
- The only way to verify identity is via ID.ME and NEVER via text messages or web forms.
- If you see this, please report or visit www.uc.pa.gov and select the “REPORT FRAUD” icon.
Below are actual messages related to PUA sent to individual cell phones:
CRITICAL Update
March 2nd, 2021
Microsoft has detected multiple 0-day exploits being used to attack on-premises versions of Microsoft Exchange Server in limited and targeted attacks. In the attacks observed, the threat actor used these vulnerabilities to access on-premises Exchange servers which enabled access to email accounts and allowed installation of additional malware to facilitate long-term access to victim environments. Microsoft Threat Intelligence Center (MSTIC) attributes this campaign with high confidence to HAFNIUM, a group assessed to be state-sponsored and operating out of China, based on observed victimology, tactics and procedures. – Microsoft
On March 3rd, the Cybersecurity Infrastructure Security Agency (CISA), issued Emergency Directive (ED) 21-02 and Alert AA21-062A addressing critical vulnerabilities in Microsoft Exchange products. - CISA
Please apply the following Microsoft patches ASAP:
CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065
COVID-19 phishing lures still working for cyber adversaries.
January 2021
COVID-19-themed cyberattacks are ongoing and now focused on big corporations, governments, and critical infrastructure. According to a recent report, the COVID-19 pandemic was a core element in phishing campaigns in 2020. Besides hacking attacks, recent incidents also involve manipulation of stolen documents in an attempt to raise doubts about the vaccine and the work of the European Medicines Agency (EMA). In the last two months, the major sectors affected by Coronavirus-themed attacks are healthcare, government, and financial services. North America, South-east Asia, and Europe were amongst the most affected regions. Scammers were found to be using social engineering emails and messaging apps to lure victims with fake claims that they can deliver COVID-19 shots within days for a price tag of $150. Last month, Pitkin County in the U.S. state of Colorado became aware of potential unauthorized access to a file including information regarding COVID-19 case investigations and contact tracing. Cybercriminals are likely to continue their Coronavirus-themed attacks taking advantage of public concern regarding the pandemic. Therefore, experts suggest organizations encrypt sensitive data, segregate networks, provide training to identify phishing emails, and stay alert while surfing online. - Cyware
Text messages promising $1,200 stimulus checks are scams, IRS warns.
December 2020
The IRS and a coalition of state tax agencies and tax industry officials are warning individuals who receive text messages promising that money is trying to lure unsuspecting individuals into providing their financial details. The text scam typically reads, “You have received a direct deposit of $1,200 from COVID-19 TREAS FUND. Further action is required to accept this payment into your account. Continue here to accept this payment…” The IRS is reminding people that it does not send these kinds of unsolicited texts or emails, never demands tax payments via gift cards nor does it threaten people with jail or lawsuits. (CNBC)
Protecting Older Adults from Contact Tracing Scams
November 2020
As COVID-19 remains a threat in the commonwealth, the Department of Aging is joining the Department of Health to warn everyone, especially older adults, about contact tracing scams. Contact tracing is the process of identifying people who came into contact with someone who has tested positive for COVID-19 so that they can quarantine and monitor for symptoms. Scammers are attempting to take advantage of how this process works by pretending to be contact tracers and trying to get personal information out of victims through phone calls or electronic messages.
A contact tracer may ask:
- For verification of someone’s date of birth, address, and any other phone numbers they may have; and
- If someone has already tested positive for COVID-19, they may also ask for the date and location of where that person was tested.
A contact tracer will never ask for:
- Social Security Numbers, financial or bank account information, or personal details unrelated to a person’s potential exposure to someone with COVID-19;
- Personal information through SMS/text message or send someone to any website link asking for personal information;
- Photographs or videos of any kind;
- Passwords; or
- Money or payment.
A contact tracer will never share a person’s information with any local, state or federal law enforcement agency. For more information about the contact tracing process, visit the Department of Health’s website.
- Pennsylvania Department of Banking and Securities
Cyber Actor Spoofing COVID-19 Loan Relief Webpage via Phishing Emails
August, 2020
The Cybersecurity and Infrastructure Security Agency issued an alert today regarding an unknown malicious cyber actor targeting small business owners through phishing emails containing links that redirect victims to a spoofed Small Business Administration COVID-19 relief webpage used to steal credentials.
The phishing email contains:
- A subject line, SBA Application – Review and Proceed
- A sender, marked as disastercustomerservice@sba[.]gov
- Text in the email body urging the recipient to click on a hyperlink to address:
- hxxps://leanproconsulting[.]com.br/gov/covid19relief/sba.gov
If you see one of these emails, delete it.
- CISA
SBA Programs - Scams and Fraud Alerts
July, 2020
Beware of Scams and Fraud Schemes
The Office of Inspector General recognizes that we are facing unprecedented times and is alerting the public about potential fraud schemes related to economic stimulus programs offered by the U.S. Small Business Administration in response to the Novel Coronavirus Pandemic (COVID-19). The Coronavirus Aid, Relief, and Economic Security Act (CARES Act), the largest financial assistance bill to date, includes provisions to help small businesses. Fraudsters have already begun targeting small business owners during these economically difficult times. Be on the lookout for grant fraud, loan fraud, and phishing.
Grants: SBA does not initiate contact on either 7a or Disaster loans or grants. If you are proactively contacted by someone claiming to be from the SBA, suspect fraud.
Loans: If you are contacted by someone promising to get the approval of an SBA loan, but requires any payment upfront or offers a high-interest bridge loan in the interim, suspect fraud.
Phishing: If you are in the process of applying for an SBA loan and receive email correspondence asking for PII, ensure that the referenced application number is consistent with the actual application number. Look out for phishing attacks/scams utilizing the SBA logo. These may be attempts to obtain your personally identifiable information (PII), to obtain personal banking access, or to install ransomware/malware on your computer.
Report Fraud:
Report any suspected fraud to OIG’s Hotline at 800-767-0385 or online at, https://www.sba.gov/about-sba/oversight-advocacy/office-inspector-general/office-inspector-general-hotline.
- Small Business Administration: https://www.sba.gov/document/report-sba-programs-scams-fraud-alerts
Coronavirus scams and malicious attacks
February 19, 2020
“Scammers are taking advantage of fears surrounding the Coronavirus," the FTC says. "They’re setting up websites to sell bogus products, and using fake emails, texts, and social media posts as a ruse to take your money and get your personal information. "The emails and posts may be promoting awareness and prevention tips, and fake information about cases in your neighborhood. "They also may be asking you to donate to victims, offering advice on unproven treatments, or contain malicious email attachments."
The FTC also provides the following measures you can take to make sure that you won't get scammed or get your computer infected with malware after falling for a scammer's tricks:
- Don’t click on links from sources you don’t know. It could download a virus onto your computer or device. Make sure the anti-malware and anti-virus software on your computer is up to date.
- Watch for emails claiming to be from the Centers for Disease Control and Prevention (CDC) or experts saying that they have information about the virus. For the most up-to-date information about the Coronavirus, visit the Centers for Disease Control and Prevention (CDC) and the World Health Organization (WHO).
- Ignore online offers for vaccinations. If you see ads touting prevention, treatment, or cure claims for the Coronavirus, ask yourself: if there’s been a medical breakthrough, would you be hearing about it for the first time through an ad or sales pitch?
- Do your homework when it comes to donations, whether through charities or crowdfunding sites. Don’t let anyone rush you into making a donation. If someone wants donations in cash, by gift card, or by wiring money, don’t do it.
- Be alert to “investment opportunities.” The U.S. Securities and Exchange Commission (SEC) is warning people about online promotions, including on social media, claiming that the products or services of publicly-traded companies can prevent, detect, or cure Coronavirus and that the stock of these companies will dramatically increase in value as a result.
-CDC & FTC
How to Avoid Small Business Scams.
November 5, 2019
There was a 424% increase in new small business cyber breaches last year. – 4iQ
- If you’re not expecting an email, and it looks suspicious email, delete it.
- Do not click links to unknown websites, and if you are asked to enter your details, including passwords and credit card details, for unverified reasons, leave the site immediately.
- Verify the company’s and supplier’s you plan on working with, check to see how long they have been in business, perform due diligence, and talk to one of their existing customers.
- Carefully check all the invoices you get, the items listed, and the business or supplier name before handing any payment. Billing schemes are ranked as the second most common fraud at 29% for organizations with fewer than 100 employees.
- Be careful about the information you give out about your business. Make sure that the person or organization you are giving it to is trustworthy and that you know what your business details will be used for.
- Limit the number of people that are authorized to order, receive invoices, and make payments for your business.
Google Confirms Serious Chrome Security Problem - Here's How To Fix It
September 17, 2019
“Google Chrome's security lead and engineering director, Justin Schuh, has warned that users of the most popular web browser should update "like right this minute." Why the urgency? Simply put, there is a zero-day vulnerability for Chrome that the Google Threat Analysis Group has determined is being actively exploited in the wild. What does that all mean? Well, a vulnerability is just a bug or flaw in the code and while they all need to be fixed, not all of them either can be or are being exploited. A zero-day vulnerability is one that threat actors have managed to create an exploit for, a way of doing bad things to your device or data before the good guys even knew the vulnerability existed. In other words, they have zero days in which to issue a fix. The bad news for users of Google Chrome is that this particular zero-day vulnerability, CVE-2019-5786, is already being exploited by the bad guys. Which is why it's so important to make sure your browser has been updated to the latest patched version that fixes the vulnerability.” - Forbes
How this can be fixed:
Luckily this is an easy problem to fix, just make sure you do it as soon as you've finished reading this! First, head over to the drop-down menu in Chrome (you'll find it at the far right of the toolbar - click on the three stacked dots) and select Help|About Google Chrome. You could also type chrome://settings/help in the address bar if you prefer, which takes you to the same dialog box. This will tell you if you have the current version running or if there is an update available. To be safe from this zero-day exploit, make sure that it says you are running version 72.0.3626.121 (Official Build). If not, then Chrome should go and fetch the latest version and update your browser for you automatically.
Previous Alert
September 1, 2019
“Google Chrome's security lead and engineering director, Justin Schuh, has warned that users of the most popular web browser should update "like right this minute." Why the urgency? Simply put, there is a zero-day vulnerability for Chrome that the Google Threat Analysis Group has determined is being actively exploited in the wild. What does that all mean? Well, a vulnerability is just a bug or flaw in the code and while they all need to be fixed, not all of them either can be or are being exploited. A zero-day vulnerability is one that threat actors have managed to create an exploit for, a way of doing bad things to your device or data before the good guys even knew the vulnerability existed. In other words, they have zero days in which to issue a fix. The bad news for users of Google Chrome is that this particular zero-day vulnerability, CVE-2019-5786, is already being exploited by the bad guys. Which is why it's so important to make sure your browser has been updated to the latest patched version that fixes the vulnerability.”


